Results 1 to 1 of 1
-
10th Jul 2014, 03:55 PM #1
 Exploit Kit Dropped Through Akamai Content Delivery Network
Exploit Kit Dropped Through Akamai Content Delivery Network
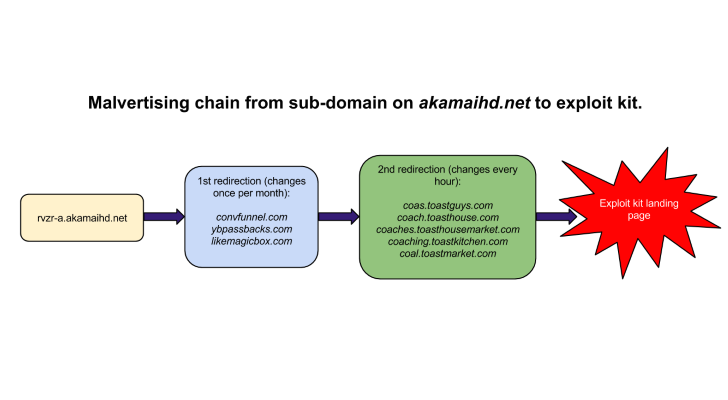
Cybercriminals abuse the Akamaihd.net content delivery network (CDN) (Alexa global rank 80) owned by Akamai Technologies to redirect users to web pages hosting exploit kits.
There is no secret that cybercriminals abuse the software affiliate marketing model by duping the user into installing potentially unwanted programs, but recent findings from Malwarebytes have revealed that the scam is also used to mask silent drive-by downloads of an exploit kit.
Jerome Segura, senior security researcher at Malwarebytes, discovered that threat actors used Akamai’s CDN to purport software updates that were in fact downloads of programs bundling affiliate software, which put money in the crooks’ pockets with each install.
This is just one side of the money-making scheme, because in some cases, a malicious “iframe” is used to redirect the victim to an exploit kit while the fake software update page is still on.
“I think the primary goal with that campaign was to hide behind these half legit - half bogus pages that claim your software may be out of date,” we were told by Segura via email. “That way, most people will only see the PUP and be oblivious about the malware.”
One of the interesting parts is that the analysis of the method has revealed that a Domain Generation Algorithm (DGA) is used to change the domains delivering the malicious pieces with a specific frequency.
According to Segura, the DGA used is a simple one that rotates the iframe every hour, with the keywords used as sub-domains being sorted alphabetically.
He also says that the malicious iframes are inserted within jQuery JavaScript library, and after an hour, the sub-domain becomes invalid and no longer responds to requests.
It appears that the exploit kit used in the scheme is Nuclear Pack, which drops a Java and a Flash Player exploit. The kit also targets vulnerabilities in Acrobat Reader and Internet Explorer. Although the products have been patched for quite some time, there are plenty of users that have not updated to the latest version.
Some of the domains appear to have been registered specifically for conducting this sort of criminal activities, because in some cases the registration day coincides with the day the domain started to be used in the malware campaign.
Malwarebytes says that Akamai Technologies has been notified of the matter last week, but no response has been received so far.
Segura says that “considering akamaihd.net is a popular CDN owned by one of the world’s largest distributed-computing platforms, it cannot be blocked by IP address without disabling legitimate traffic as well.”Kepler Reviewed by Kepler on . Exploit Kit Dropped Through Akamai Content Delivery Network http://i1-news.softpedia-static.com/images/news-700/Exploit-Kit-Dropped-Through-Akamai-Content-Delivery-Network.jpg Cybercriminals abuse the Akamaihd.net content delivery network (CDN) (Alexa global rank 80) owned by Akamai Technologies to redirect users to web pages hosting exploit kits. There is no secret that cybercriminals abuse the software affiliate marketing model by duping the user into installing potentially unwanted programs, but recent findings from Malwarebytes have Rating: 5
Sponsored Links
Thread Information
Users Browsing this Thread
There are currently 1 users browsing this thread. (0 members and 1 guests)
Similar Threads
-
Dailymotion.com Visitors Redirected to Exploit Kit
By Kepler in forum News & Current EventsReplies: 0Last Post: 6th Jul 2014, 01:49 PM -
CashMyLinks - Private Pay Per Install Content Locking Network
By CML-Mike in forum Affiliate Programs PromotionReplies: 7Last Post: 26th Sep 2012, 10:47 AM -
Leadzup.com Content Locking Network
By Leadzup|sam in forum Affiliate Programs PromotionReplies: 0Last Post: 17th Jul 2012, 04:34 PM -
[Selling] Advertise through our network - Very Cheap - Starting from $0.5
By Bose in forum Completed TransactionsReplies: 23Last Post: 2nd Feb 2011, 11:35 AM -
[Spcash Network] Monetize All Types Of Contents - Pay For Both Quality & Bad Traffic
By spcash in forum File Host DiscussionReplies: 2Last Post: 14th Jan 2011, 10:25 AM













 Register To Reply
Register To Reply






 Staff Online
Staff Online
themaRegister - register to forums...
Version 3.39 released. Open older version (or...